Nx Platform Overview
User Management
Dashboards Overview
Data Risks
Dashboard Filters, Queries and Customization
Dark Data Classification
Access Activity Risks
Perform the following steps to review Access Risk:
- As access risk is primarily associated with sensitive data (e.g., Confidential or Restricted), we recommend excluding non-sensitive files (e.g., Internal or Public) as they typically do not pose a material risk concern. This also assists in having a stronger focus to more efficiently assess key access risks.
Next, select whatever account (e.g., user, title, group or departmental) or folder or file you’re looking to assess.
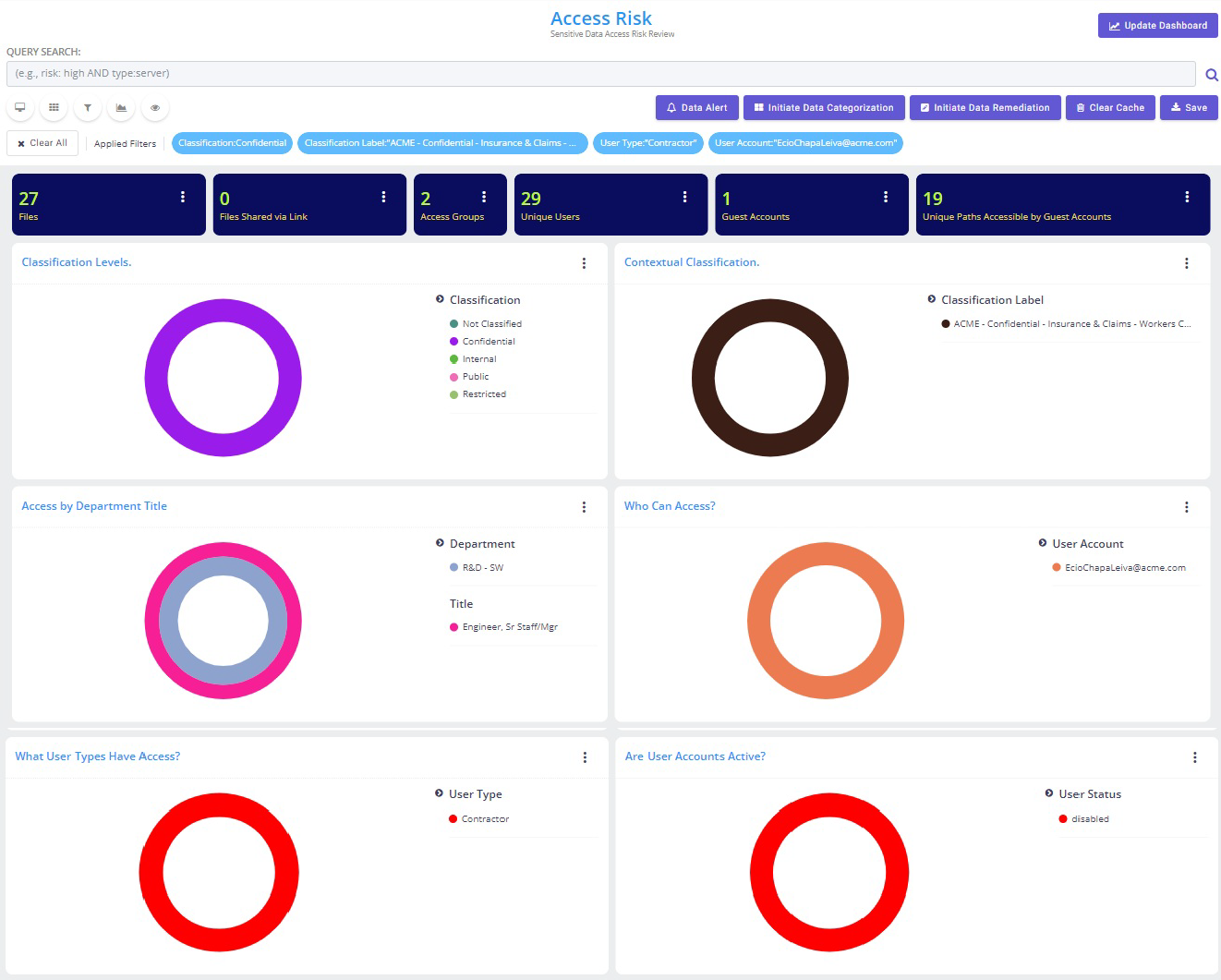
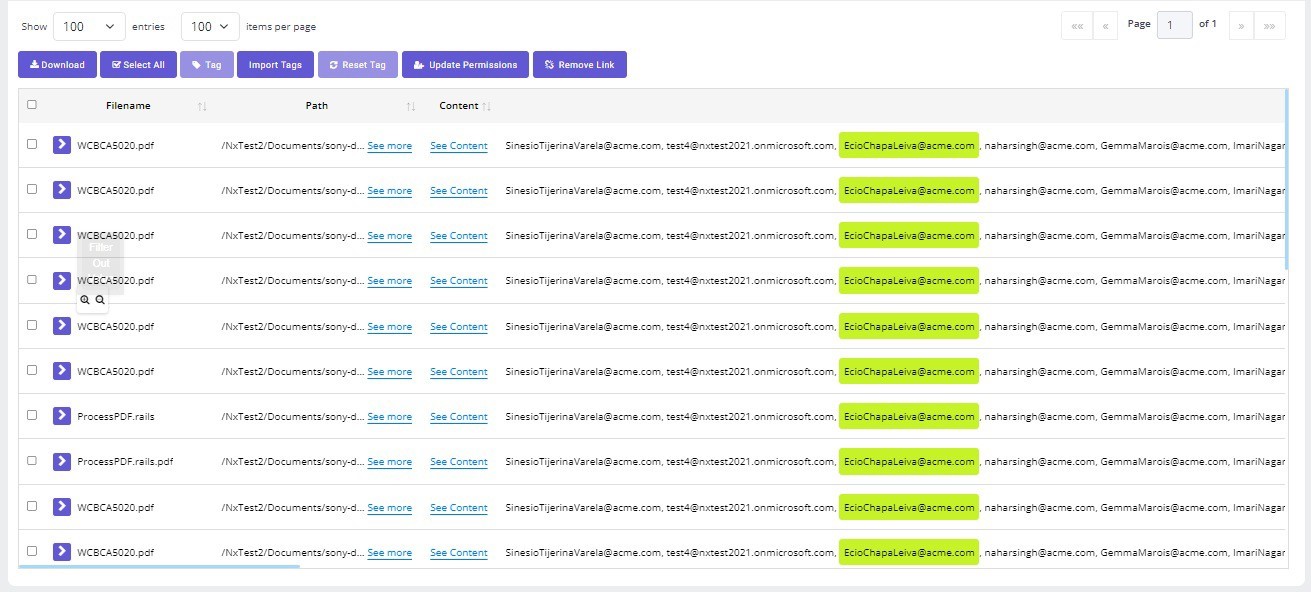
In the example above, the key access risk identifies the following risk factors for User Account [email protected]:
- Held the position of Engineer with R&D department
- Is a contractor and his account is disabled
- The 27 files that were classified as Acme-Confidential-Insurance & Claims-Workers Comp
- The associated files contain SSNs, Address, Email Addresses and Phone Numbers